SPE1.1.0.2
SYSTEM SETTINGS

CONTENTS
PROCESS SETTINGS
Basic settings for file and folders destruction are set in the control panel of application.
The panel allows entering the following types of settings:
- Hardware dependecy - Dependency of the processes on the particular device.
- Backup the files in package - Backup the files described in the file package.
- Files packages - Current directory where the file packages are stored.
- Backup directory - Directory where the backups of the files saved in the selected packages will be saved.
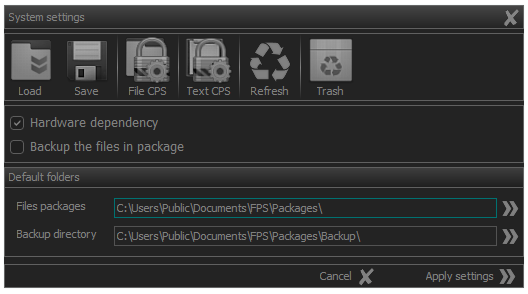
Fig.1. System settings panel (FDM-SE edition).
The following table describes the main settings related to each element of the process execution.
| Settings | Description | Options |
|
Hardware dependency |
All processes will be tied to a used (or specific) hardware system. In this case, it is not possible to processed data on a computer (server or mobile device) other than the one on which the packages a created. |
On/Off |
|
Backup the source files |
Before destroing (encrypting or decrypting) of the files and directories, they will be stored in their original form in a directory selected by the operator. This directory can be located on a local drive, on a server, or in the cloud. The directory is specified in the Backup directory field. |
On/Off |
Note: In the professional versions of the system, the backup copies are stored in secure file containers, and in the corporate versions, hybrid server solutions are used for this purpose.
FILE ENCRYPTION SETTINGS
Activation of the system panel for entering file and directory encryption parameters is done by clicking the File CPS (File Crypto Process Setting) button as shown in the image) or using the [ Ctrl + F7 ] key combination.
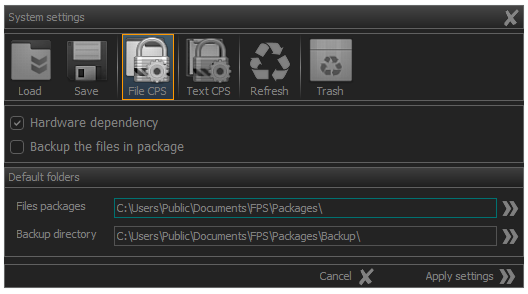
Fig.2. File crypto process setting (CPS) activation.
As a result, the system panel will be activated for entering and checking the crypto primitives that will be used to encrypt files and directories.
This panel is used to create and analyze different combinations of crypto primitives, which, after being confirmed, are used in the process of encrypting files and directories.
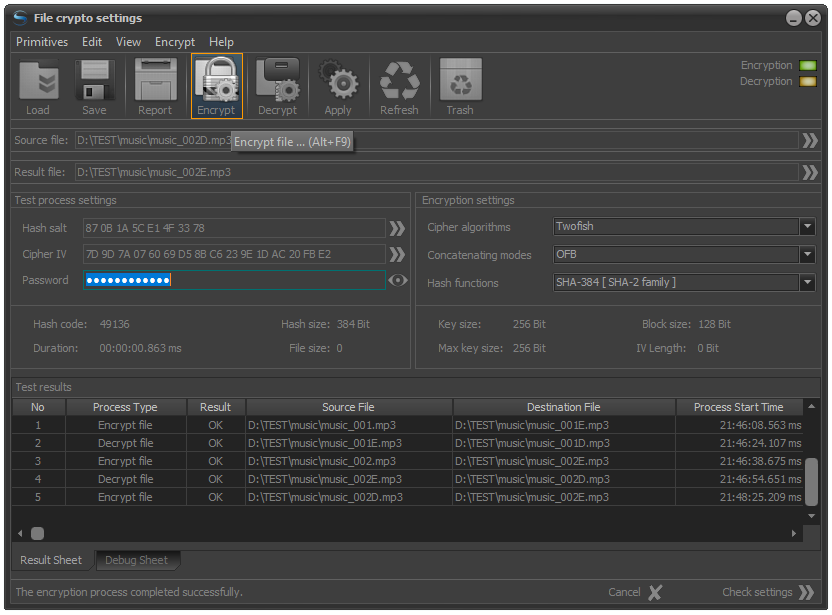
Fig.3. File crypto setting panel.
Note: Detailed information on what are the best practices when choosing crypto primitives used in the process of encrypting files can be found in the relevant section or on the dedicated FPS forum.
TEXT ENCRYPTION SETTINGS
Setting up the combination of crypto primitives for text encryption (text documents, database fields, secure messages, etc.) is done in a way that is analogous to setting up file and directory encryption.
The difference in this case is that testing will encrypt text.
Activation of the system panel for entering file and directory encryption parameters is done by clicking the Text CPS (Text Crypto Process Setting) button as shown in the image) or using the [ Ctrl + F8 ] key combination.
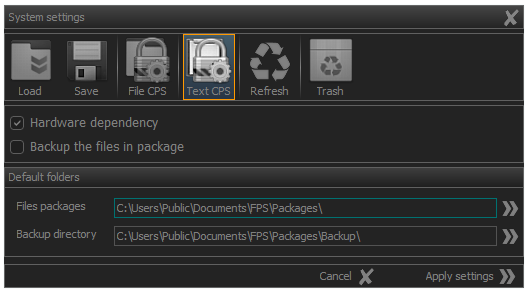
Fig.4. Text crypto primitives setting activation.
As a result, the system panel will be activated for entering and checking the crypto primitives that will be used to encrypt text (strings).
This panel is used to create and analyze different combinations of crypto primitives, which, after being confirmed, are used in the process of encrypting string or text messages.
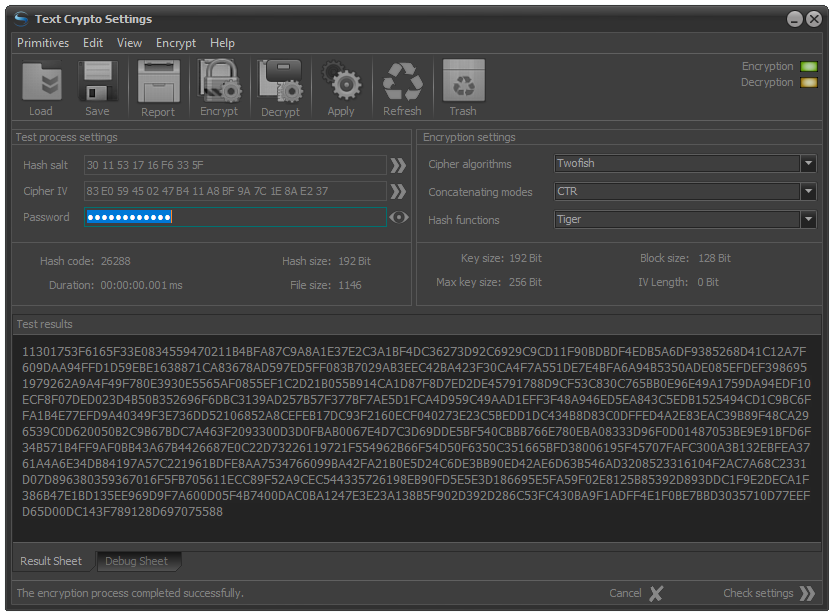
Fig.5. Text crypto setting panel.
Note: By default, text in UTF-8 format is entered in the text field of the module for choosing a combination of crypto primitives for encrypting character strings, which has the form:
This is a test for digital data encryption.
Это тест на шифрование цифровых данных.
這是對數字數據加密的測試。
これは、デジタルデータ暗号化のテストです。
이것은 디지털 데이터 암호화 테스트입니다.
هذا اختبار لتشفير البيانات الرقمية.
Bu, dijital veri şifreleme için bir testtir.
זוהי בדיקה להצפנת נתונים דיגיטליים.
This ensures that the system can be used to encrypt messages written in different languages.
SET CONTROL FUNCTIONS
Control over system processes is implemented by recording in real time the results of the execution of the selected function in control tables.
The selection of which fields to visualize is done by selecting View > Crypto process table ... from the control panel's main menu, then selecting the fields to be monitored
For example, if the operator wants to display the field containing information about the length in bytes of the secret key used, he should select View > Crypto process table ... > Cipher information ... and check a field Key size.
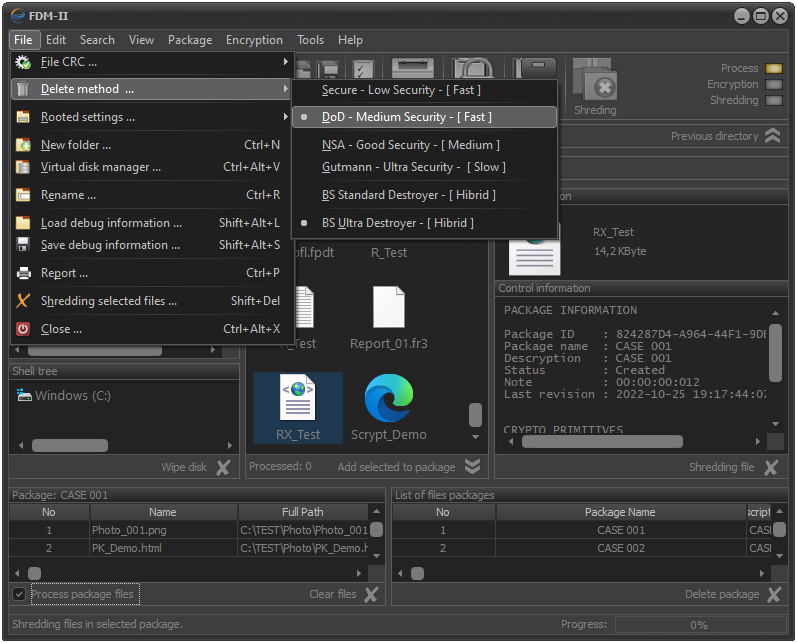
Fig.6. Crypto process control settings.
Information from control tables is automatically converted into system reports.
System reports are an extremely useful tool for documenting the creation, management, encryption, storage and destruction of digital data.
Fig.7. Crypto process system report.
One of the advantages of system reports is that they can be converted according to specific needs.
In the standard versions of FPS, reports can be converted to the following formats:
- PDF - Portable Document Format (*.PDF);
- RTF - Rich Text Format (*.RTF);
- TXT - Standard Text Document (*.TXT);
- HTML - Hypertext Markup Language (*.HTML);
- XML - Extensible Markup Language (*.XML)
- CSV - Comma-Separated Values (*.CSV).
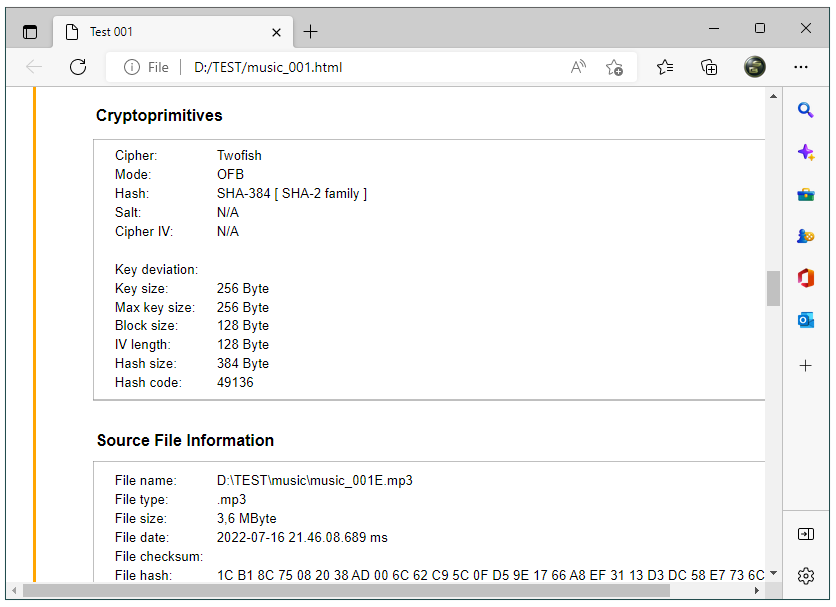
Fig.8. Convert system report to HTML.
Contents