SPE1.1.0.2
DISK SANITIZATION METHODS

CONTENTS
SUMMARY
Disk sanitization is the process of physically obliterating data by overwriting disks or SSDs with specified byte patterns or random data so that recovery of the original data becomes impossible.
Using the sanitization process ensures that no one can recover the data on the disks.
The disk sanitization process uses three successive default or user-specified byte overwrite patterns for up to seven cycles per operation. The random overwrite pattern is repeated for each cycle.
CRYPTOGRAPHIC ERASURE
This data sanitization method involves the use of system encryption software to sanitize data.
Cryptographic erasure works by using encryption software, whether built-in or manually deployed, on the entire set of data on the storage device, then deleting the key that would have been used to decrypt the data.
Тhe encryption algorithm must be a minimum of 128 bits and lists the following steps to ensure proper data sanitization through cryptographic erasure:
- Cryptographic erasure can only be supported when the encryption on the data storage device is on and access to the API call to the said device is granted to remove the key.
- This method must ensure that the encryption key has successfully replaced the old key with a new one, thereby rendering the data encrypted by that key and the old key itself unrecoverable.
- An inviolable certificate must be provided by the cryptographic erasure software that asserts that the key, device data, and standards have been removed.
DATA MASCING
Data masking is a widely used technique in compliance strategies and is explicitly required by some compliance standards.
Masking involves creating fake versions of the data, which retain structural properties of the original data (for example, replacing real customer names with other, randomly-selected names).
Masking techniques include character shuffling, word replacement, and randomization. What is common to all these techniques is that the masked version of the data cannot be reverse engineered to obtain the original data values.
Data masking is highly effective for sanitization. Effectively, it sanitizes data on the device while it is still in use. The key advantages of sanitization compared to other techniques are:
- Quick and easy to implement.
- Complies with most regulations and standards.
- Can be applied on an ongoing basis to existing data.
- Does not require a special sanitization policy for decommissioned devices—unless they contain unmasked data.
DATA ERASURE
Data erasure, considered the highest form of securing data within data sanitization techniques, is software that writes over all the data with zeros and ones.
This renders the data unrecoverable and achieves data sanitization on the storage device.
To achieve successful sanitization, data erasure software must do the following:
- Data erasure software must let choose a specific standard and sanitization method.
- Selected data sanitization method must guarantee and verify that data erasure has been successful and that the overwriting methodology has removed all targeted data.
- An inviolable certificate must be provided by the data erasure software that asserts that the key, device data, and standards have been removed.
The National Institute of Standards and Technology (NIST) defines sanitization as: "the general process of removing data from storage media, such that there is reasonable assurance that the data may not be easily retrieved and reconstructed."
Categories of Media Sanitization
| Method | NIST 800-88 Description |
|
Clearing |
Clearing information is a level of media sanitization that would protect the confidentiality of information against a robust keyboard attack. Simple deletion of items would not suffice for clearing. Clearing must not allow information to be retrieved by data, disk, or file recovery utilities. It must be resistant to keystroke recovery attempts executed from standard input devices and from data scavenging tools. For example, overwriting is an acceptable method for clearing media. |
|
Purging |
Purging information is a media sanitization process that protects the confidentiality of information against a laboratory attack. For some media, clearing media would not suffice for purging. However, for Advanced Technology Attachment (ATA) disk drives manufactured after 2001 (over 15 GB) the terms clearing and purging have converged. A laboratory attack would involve a threat with the resources and knowledge to use nonstandard systems to conduct data recovery attempts on media outside their normal operating environment. This type of attack involves using signal processing equipment and specially trained personnel. Executing the firmware Secure Erase command (for ATA drives only) and degaussing are examples of acceptable methods for purging. |
|
Destroying |
Destruction of media is the ultimate form of sanitization. After media are destroyed, they cannot be reused as originally intended. Physical destruction can be accomplished using a variety of methods, including disintegration, incineration, pulverizing, shredding and melting. |
The type of sanitization performed depends on two factors:
- If the media will be reused, and will not be leaving organization control, then clearing is a sufficient method of sanitization.
- If the media will be reused and repurposed for a non critical function and/or will be leaving organization control, (i.e., media being exchanged for warranty, cost rebate, or other purposes and where the specific media will not be returned to the agency), then purging should be selected as the sanitization method.
If the media will not be reused at all, then destroying is the method for data sanitization.
Note: MDF is characterized by the use of hybrid technologies that allow easy access to the remediation processes, which have different levels of guaranteed security.MASTER FILE TABLE (MFT)
MFT stands for Master File Table, and it is an alternative to the NTFS file system that is the conventional file system for hard drive partitions.
The NTFS file system contains a file called the master file table, or MFT. All information about a file, including its size, time and date stamps, permissions, and data content, is stored either in MFT entries, or in space outside the MFT that is described by MFT entries.
The work of MFT is to manage logs of the entire document that is accessible through the partition.
As files are added to an NTFS file system volume, more entries are added to the MFT and the MFT increases in size. When files are deleted from an NTFS file system volume, their MFT entries are marked as free and may be reused. However, disk space that has been allocated for these entries is not reallocated, and the size of the MFT does not decrease.
The NTFS file system reserves space for the MFT to keep the MFT as contiguous as possible as it grows. The space reserved by the NTFS file system for the MFT in each volume is called the MFT zone. Space for file and directories are also allocated from this space, but only after all of the volume space outside of the MFT zone has been allocated.
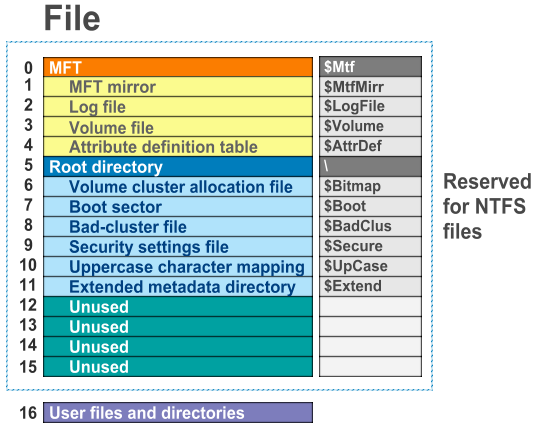
Fig.1. Master file table (MFT) structure.
MTF has everything that a recovery software needs to recover lost ones.
When the document is deleted, its entry is marked inside the MFT, which gives all the precise data about the document. Also, the space taken by the Master File Table is marked as free storage, so that no storage is hindered after deleting.
The removing all the MFT tables will make it impossible to recover crytical data.
MTF Eracer is a tool that is built into the application to prevent disk recovery and free up data from unused disk space. It replaces all the free space with zeros, and thus, there is nothing left to recover.
Contents