LE1.1.0.2
STANDARD ENCRYPTION

CONTENTS
DEFINITION
Standard encryption is the process of using an algorithm to transform digital information or signals into cypher data in order to ensure that sensitive information remains unreadable to unauthorized users.
Encrypted data usually looks like a long sequence of random letters and numbers. Once data is encrypted, it can only be turned back into understandable available information and made readable again by using the correct encryption key.
Encryption is the basic building block of data security. It is the simplest and most important way to ensure a computer system's information can't be stolen and read by someone who wants to use it for malicious purposes.
Data security encryption is widely used by individual users and large corporations to protect user information sent between a browser and a server. That information could include everything from payment data to personal information. Data encryption software, also known as an encryption algorithm or cipher, is used to develop an encryption scheme that theoretically can only be broken with large amounts of computing power.
Encryption is essential for ensuring the trusted delivery and storage of sensitive information.
Stream ciphers, which are used mostly for real-time communications, encrypt data one bit or byte at a time.
Block ciphers break data into larger segments, typically about 64 bits, before encrypting it.
Encryption involves using a cryptographic key, a set of mathematical values both the sender and recipient agree on. The recipient uses the key to decrypt the data, turning it back into readable data.
The more complex the cryptographic key, the more secure the encryption – because third parties are less likely to decrypt it via brute force attacks (i.e. trying random numbers until the correct combination is guessed).
Encryption is also used to protect passwords. Password encryption methods scramble your password, so it's unreadable by unauthorized users.
STANDARD ENCRYPTION METHODS
The two most common encryption methods are symmetric and asymmetric encryption.
The names refer to whether or not the same key is used for encryption and decryption.
Symmetric encryption keys
This is also known as private key encryption. The key used to encode is the same as the one used to decode, making it best for individual users and closed systems. Otherwise, the key must be sent to the receiver. This increases the risk of compromise if it's intercepted by a third party.
Note: This method is faster than the asymmetric method.
Asymmetric encryption keys
This type uses two different keys — public and private — that are linked together mathematically.
The keys are essentially large numbers that have been paired with each other but aren't identical, hence the term asymmetric.
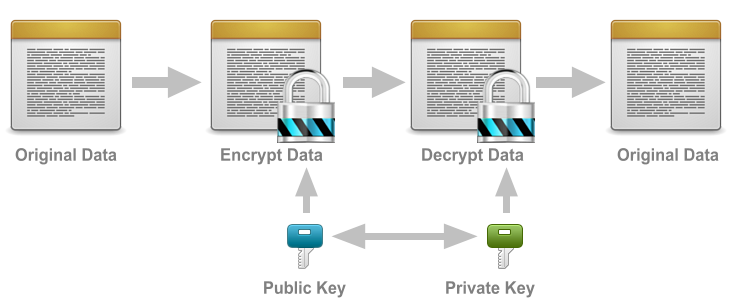
The private key is kept secret by the owner, and the public key is either shared amongst authorized recipients or made available to the public at large.
Note: Data encrypted with the recipient’s public key can only be decrypted with the corresponding private key.
CRYPTOGRAPHIC PRIMITIVES
Cryptographic primitives are well-established, low-level cryptographic algorithms that areused to build cryptographic protocols for data security systems.
The set of cryptographic primitives forms the cryptographic mechanism that is used for standard data encryption.
Each of the crypto primitives (if used without combining with others) is not able to guarantee a sufficiently high degree of protection.
For instance, a bare encryption algorithm will provide no authentication mechanism, nor any explicit message integrity checking.
Only when combined in security protocols, can more than one security requirement be addressed.
For example, to transmit a message that is not only encoded but also protected (i.e. it is confidential and integrity-protected), an encoding routine, such as DES, and a hash-routine such as SHA-1 can be used in combination. If the attacker does not know the encryption key, they can not modify the message such that message digest value(s) would be valid.
Combining cryptographic primitives to make a security protocol is itself an entire specialization.
Most exploitable errors (i.e., insecurities in crypto systems) are due not to design errors in the primitives (assuming always that they were chosen with care), but to the way they are used, i.e. bad protocol design and buggy or not careful enough implementation.
The following base crypto primitives are used in the public versions of File Protect System:
- Cipher algorithms - Algorithms for encrypting and decrypting data.
- Block concatenating modes - Algorithm that uses a block cipher to provide information security such as confidentiality or authenticity.
- Hash algorithms - Mathematical algorithm that maps data of an arbitrary size (often called the "message") to a bit array of a fixed size (the "hash value", "hash", or "message digest").
- Key derivation function (KDF) - Cryptographic algorithm that derives one or more secret keys from a secret value such as a main key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher).
- Message authentication algorithms (MAA) - Cryptographic functions for computing a message authentication code (MAC).
- Cyclic redundancy check (CRC) - Error-detecting code commonly used in digital networks and storage devices to detect accidental changes to digital data. Blocks of data entering these systems get a short check value attached, based on the remainder of a polynomial division of their contents.
PERSONAL AUTHETICATION CERTIFICATES
Personal authentication certificates are used for client authentication.
A personal authentication certificate, which is also known as a client certificate, authenticates users within an organizational setup. Using these types of certificates enable you to restrict access to sensitive data or systems to only select individuals. Companies install these certs on end user devices as a means of access control and passwordless authentication. Employees can access those resources only when they log in from the office device that has the certificate.
Some resources, email clients, and websites (such as intranet sites, development and testing sites, or even the admin pages of the public-facing sites) are intended for only employees to use. And it’s always a good practice to restrict outsiders’ access to these web pages. That’s where a personal authentication certificate and asymmetric encryption come in handy.
Contents