SPE1.1.0.2
BLOCK CIPHER MODE

CONTENTS
- Modes of operation
- Padding
- Authenticated encryption with additional data (AEAD) modes
- Cipher block chanining (CBC)
- Cipher feedback (CFB)
- Output feedback (OFB)
- Counter (CTR)
- Block cipher mode chpice
MODES OF OPERATION
In cryptography, a block cipher mode of operation is an algorithm that uses a block cipher to provide information security such as confidentiality or authenticity.
A block cipher by itself is only suitable for the secure cryptographic transformation (encryption or decryption) of one fixed-length group of bits called a block. A mode of operation describes how to repeatedly apply a cipher's single-block operation to securely transform amounts of data larger than a block.
Most modes require a unique binary sequence, often called an initialization vector (IV), for each encryption operation.
The IV has to be non-repeating and, for some modes, random as well. The initialization vector is used to ensure distinct ciphertexts are produced even when the same plaintext is encrypted multiple times independently with the same key.
Some modern modes of operation combine confidentiality and authenticity in an efficient way, and are known as authenticated encryption modes.
PADDING
A block cipher works on units of a fixed size (known as a block size), but messages come in a variety of lengths.
So some modes (namely ECB and CBC) require that the final block be padded before encryption.
Several padding schemes exist. The simplest is to add null bytes to the plaintext to bring its length up to a multiple of the block size, but care must be taken that the original length of the plaintext can be recovered; this is trivial, for example, if the plaintext is a C style string which contains no null bytes except at the end.
Slightly more complex is the original DES method, which is to add a single one bit, followed by enough zero bits to fill out the block; if the message ends on a block boundary, a whole padding block will be added.
Most sophisticated are CBC-specific schemes such as ciphertext stealing or residual block termination, which do not cause any extra ciphertext, at the expense of some additional complexity.
Schneier and Ferguson suggest two possibilities, both simple: append a byte with value 128 (hex 80), followed by as many zero bytes as needed to fill the last block, or pad the last block with n bytes all with value n.
CFB, OFB and CTR modes do not require any special measures to handle messages whose lengths are not multiples of the block size, since the modes work by XORing the plaintext with the output of the block cipher.
The last partial block of source data is XORed with the first few bytes of the last keystream block, producing a final ciphertext block that is the same size as the final partial plaintext block.
Note:
This characteristic of stream ciphers makes them suitable for applications that require the encrypted ciphertext data to be the same size as the original plaintext data, and for applications that transmit data in streaming form where it is inconvenient to add padding bytes.
AUTHENTICATED ENCRYPTION WITH ADDITIONAL DATA (AEAD) MODES
A number of modes of operation have been designed to combine secrecy and authentication in a single cryptographic primitive.
Examples of such modes are extended cipher block chaining (XCBC), integrity-aware cipher block chaining (IACBC), integrity-aware parallelizable mode (IAPM), OCB, EAX, CWC, CCM, and GCM.
Authenticated encryption modes are classified as single-pass modes or double-pass modes.
Some single-pass authenticated encryption algorithms, such as OCB mode, are encumbered by patents, while others were specifically designed and released in a way to avoid such encumberment.
In addition, some modes also allow for the authentication of unencrypted associated data, and these are called AEAD (authenticated encryption with associated data) schemes. For example, EAX mode is a double-pass AEAD scheme while OCB mode is single-pass.
CIPHER BLOCK CHAINING (CBC)
CBC has been the most commonly used mode of operation.
Its main drawbacks are that encryption is sequential (i.e., it cannot be parallelized), and that the message must be padded to a multiple of the cipher block size. One way to handle this last issue is through the method known as ciphertext stealing. Note that a one-bit change in a plaintext or initialization vector (IV) affects all following ciphertext blocks.
Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but subsequent plaintext blocks will be correct. This is because each block is XORed with the ciphertext of the previous block, not the plaintext, so one does not need to decrypt the previous block before using it as the IV for the decryption of the current one.
This means that a plaintext block can be recovered from two adjacent blocks of ciphertext. As a consequence, decryption can be parallelized.
Note that a one-bit change to the ciphertext causes complete corruption of the corresponding block of plaintext, and inverts the corresponding bit in the following block of plaintext, but the rest of the blocks remain intact.
Explicit initialization vectors[24] takes advantage of this property by prepending a single random block to the plaintext.
Encryption is done as normal, except the IV does not need to be communicated to the decryption routine.
Note:
Whatever IV decryption uses, only the random block is "corrupted". It can be safely discarded and the rest of the decryption is the original plaintext.
CIPHER FEEDBACK (CFB)
The cipher feedback (CFB) mode, in its simplest form uses the entire output of the block cipher.
In this variation, it is very similar to CBC, makes a block cipher into a self-synchronizing stream cipher.
NIST SP800-38A defines CFB with a bit-width. The CFB mode also requires an integer parameter, denoted s, such that 1 ≤ s ≤ Block Size (CFB-1, CFB-8, CFB-64, CFB-128, etc.).
The value of s is sometimes incorporated into the name of the mode, e.g., the 1-bit CFB mode, the 8-bit CFB mode, the 64-bit CFB mode, or the 128-bit CFB mode.
CFB-1 is considered self synchronizing and resilient to loss of cipherdata. When the 1-bit CFB mode is used, then the synchronization is automatically restored b+1 positions after the inserted or deleted bit.
For other values of s in the CFB mode, and for the other confidentiality modes in this recommendation, the synchronization must be restored externally." (NIST SP800-38A). I.e. 1-bit loss in a 128-bit-wide block cipher like AES will render 129 invalid bits before emitting valid bits.
CFB may also self synchronize in some special cases other than those specified. For example, a one bit change in CFB-128 with an underlying 128 bit block cipher, will re-synchronize after two blocks. (However, CFB-128 etc. will not handle bit loss gracefully. A one-bit loss will cause the decryptor to lose alignment with the encryptor).
OUTPUT FEEDBACK (OFB)
The output feedback (OFB) mode makes a block cipher into a synchronous stream cipher.
It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext.
Just as with other stream ciphers, flipping a bit in the cipherdata produces a flipped bit in the plaintext at the same location. This property allows many error-correcting codes to function normally even when applied before encryption.
Each output feedback block cipher operation depends on all previous ones, and so cannot be performed in parallel. However, because the plaintext or cipherdata is only used for the final XOR, the block cipher operations may be performed in advance, allowing the final step to be performed in parallel once the source data or ciphertext is available.
It is possible to obtain an OFB mode keystream by using CBC mode with a constant string of zeroes as input. This can be useful, because it allows the usage of fast hardware implementations of CBC mode for OFB mode encryption.
Using OFB mode with a partial block as feedback like CFB mode reduces the average cycle length by a factor of 232 or more. A mathematical model proposed by Davies and Parkin and substantiated by experimental results showed that only with full feedback an average cycle length near to the obtainable maximum can be achieved. For this reason, support for truncated feedback was removed from the specification of OFB.
COUNTER (CTR)
Like OFB, counter mode turns a block cipher into a stream cipher. It generates the next keystream block by encrypting successive values of a "counter".
The counter can be any function which produces a sequence which is guaranteed not to repeat for a long time, although an actual increment-by-one counter is the simplest and most popular.
The usage of a simple deterministic input function used to be controversial; critics argued that "deliberately exposing a cryptosystem to a known systematic input represents an unnecessary risk". However, today CTR mode is widely accepted, and any problems are considered a weakness of the underlying block cipher, which is expected to be secure regardless of systemic bias in its input.
CTR mode has similar characteristics to OFB, but also allows a random-access property during decryption.
CTR mode is well suited to operate on a multi-processor machine, where blocks can be encrypted in parallel. Furthermore, it does not suffer from the short-cycle problem that can affect OFB.
If the IV/nonce is random, then they can be combined with the counter using any invertible operation (concatenation, addition, or XOR) to produce the actual unique counter block for encryption. In case of a non-random nonce (such as a packet counter), the nonce and counter should be concatenated (e.g., storing the nonce in the upper 64 bits and the counter in the lower 64 bits of a 128-bit counter block).
Simply adding or XORing the nonce and counter into a single value would break the security under a chosen-plaintext attack in many cases, since the attacker may be able to manipulate the entire IV–counter pair to cause a collision.
Note:
CTR mode (CM) is also known as integer counter mode (ICM) and segmented integer counter (SIC) mode.
BLOCK CIPHER MODE CHOICE
The choice of block cipher mode is a base component in configuring the used crypto primitives.
If a block cipher is used, the system automatically generates an IV, the size of which is directly dependent on the type of the selected algorithm.
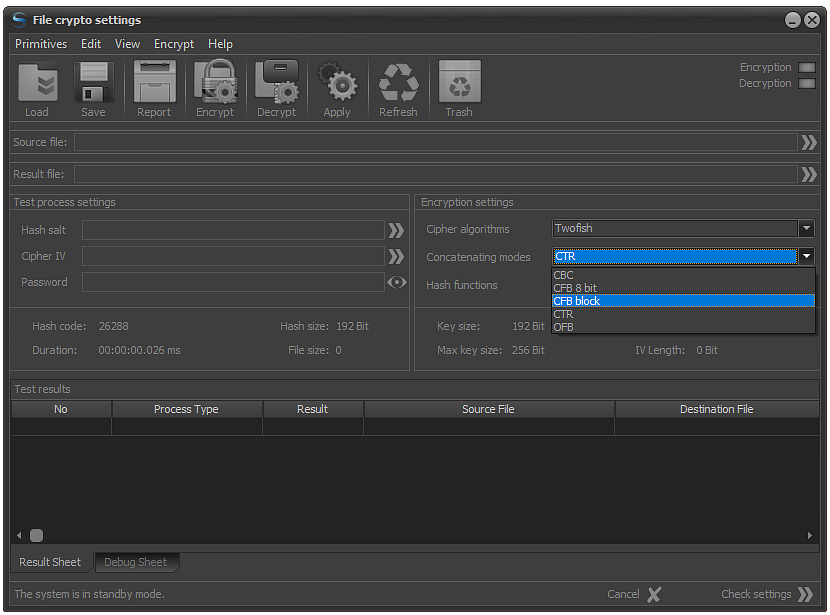
Fig.1. Block cipher mode choise.
Block cipher mode selection is done by selecting the algorithm from the list of standard algorithms in the Block cipher mode combo box located in the Encrypted settings panel.
Note: Only block cipher mode that have proven their reliability and crypto resistance are used in BS applications.
Standard Block Cipher Modes
- ECB - Electronic code book (RFC 5830);
- CBC - Block cipher mode of operation (RFC 2451);
- CTS - Ciphertext stealing (RFC 3962);
- CTS3 - Ciphertext stealing (RFC 3962);
- CFB8 - Cipher feedback (RFC 2950);
- CFB - Cipher feedback (RFC 2950);
- OFB8 - Output feedback (RFC 2948);
- OFB - Output feedback (RFC 2948);
- CFS8 - Cryptographic file system (RFC 2628);
- CFS - Cryptographic file system (RFC 2628).
Note: The number of block cipher mode used is different for the standard and advanced versions of the crypto primitives configuration module. Only block cipher mode that have proven their reliability and crypto resistance are used in BS applications.
Contents < Previous Next >