SPE1.1.0.2
FILE PACKAGES

CONTENTS
DESCRYPTION
File bundles are spreadsheets that contain meta information about files and directories that are physically located on one or more physical devices.
There are two types of file packages as follows:
- Local file packages;
- Server file packages.
Local file packages are local spreadsheets (or local databases) containing information about the files that are described in them. The main components of this information include the physical address of the file, its parameters, control markers, as well as data about the processes performed with the file.
Server file packages are components of specialized, databases located on secure servers. This type of solution is used in enterprise versions of the application. What is important to understand that in this case, file bundles can be considered as highly secure, hybrid cloud solutions.
Regardless of whether the application uses local or server file packages, the important thing to know is that they only contain information about the files and directories, not the files themselves.
Note: In the event that a file is removed from the physical drive or modified or encrypted for any reason, information about this will be reflected in the file package, then and only then, when a content monitoring process is initiated.
USE OF FILE PACKAGES
File packages are a tool for executing meta-scenarios related to processing critical data.
File packages are a major component in the practical implementation of File integrity monitoring, over local, network and/or server files and directories, as well as those that are physically located on external media, including and mobile devices.
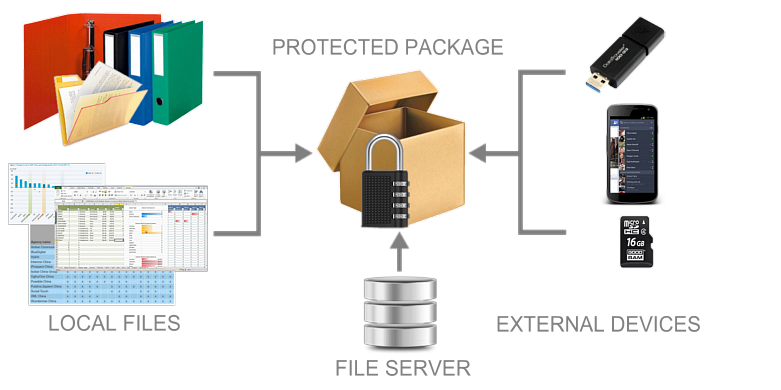
Fig.1. Sources of information when forming a file package.
The actions that can be performed on the files, the information about which is recorded in the package, are as follows:
- File integrity check;
- File modification control;
- Checking the current status of files and directories;
- Checking the current status of files and directories;
- Encrypting the files in the package;
- Decrypting the files in the package;
- Mutual overlapping of the files in the package;
- Shredding and/or sanitizing the files saved in the package etc.
All operations on the files and folders saved in the package are performed only when the files and folders are physically accessible. If they cannot be accessed (deleted, physically inaccessible network drive or other reason), this will be reflected in the packet, recording the time when this finding was made.
If encryption is performed on the files in the package, all accessible files will be encrypted using the selected crypto primitives.
However, if the files are removed, it is possible, before this is implemented, to encrypt the files using a randomly selected combination of cryptographic primitives. In this case, in addition to encryption, bitwise replacement of the content with random bits is also performed.
Note: Higher versions of the product perform random obfuscation of files, but this process is more of a recommendation and is only applied to critical data with high confidentiality requirements.
EXPORTING FILE PACKAGES
Whether file packages are local or server-side, they can be exported to spreadsheets in a variety of formats.
The information contained in the exported data can be stored both in an encrypted (protected) form and in an unencrypted form. Encryption of spreadsheets is recommended when they are saved on devices that can only be accessed by a single user, during data transfer, and in case of critical information for official use.
Note: The metadata used in the application is used not only to check the integrity of files, but also in the planning and execution of periodically repeating processes. For this reason, metadata encryption is recommended.
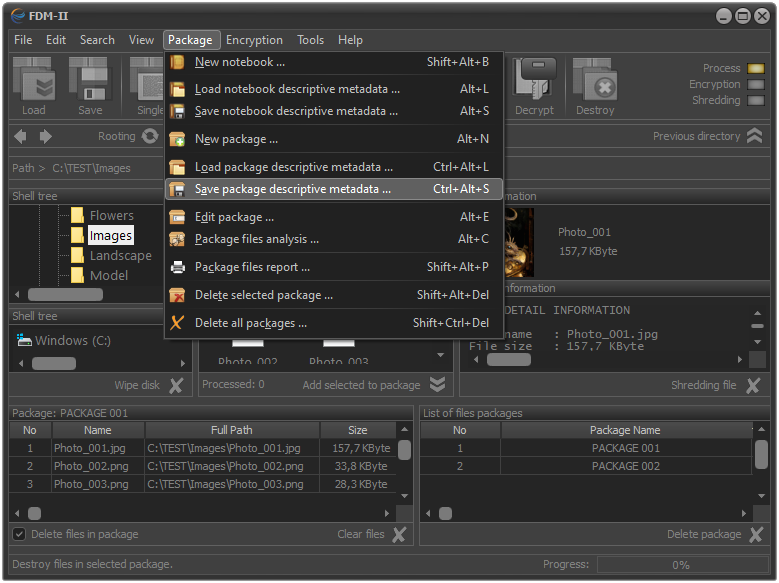
Fig.2. Exported metainformation in selected package.
In order for the meta information in the file package to be exported, we need to select Package - Save package descryptive metadata from the main menu (as shown in the image) or press a Ctrl+Alt+S key combination.
The application allows exporting the file packages to local spreadsheets in the following format:
- File Package Metadata (*.fpd);
- File Package Information (*.fpi);
- Binary File (*.fds);
- Local Database File (*.fdb);
- Associated Database (*.adb);
- Client Data Set Table (*.cds);
- JavaScript Object Notation (*.json);
- Extensible Markup Language (*.xml) etc.
The security policy at Balck Screen requires that each package be identified by a unique number. This applies to both on-premises and server solutions.
In enterprise versions of the application, in addition to a digital identifier, each of the packages contains a unique key that binds the used package to a specific physical device. This is a basic element of the application's built-in DLP system.
Note: By default, file packages are exported in File Package Metadata (*.fpd) format.
METADATA PROTECTION
In higher versions of the application, the file meta-information contained in the packages can be protected by encryption.
In order for the meta information in the file package to be encrypted, we need to select Encryption - Encryption meta information from the main menu or press a F9 key.
Another possibility is to click on the button Encrupt, located on the control panel.
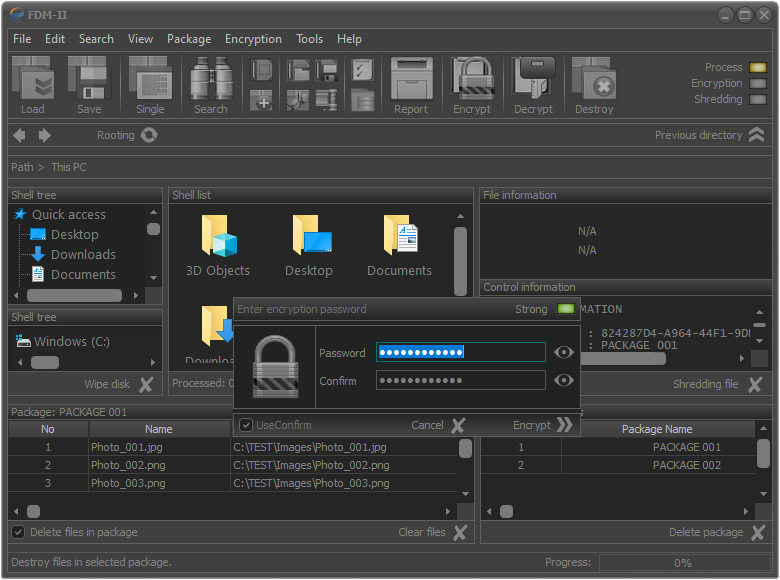
Fig.3. Standard encryption of the information in the package.
The encryption of the meta-information contained in the file package does not affect the physical file in any way. Whether the package is encrypted or not, the file retains its state. The file will only be encrypted if explicitly indicated or as an auxiliary function in the destruction process.
As a result of these actions, a user password input module will be activated. In the process of entering the password, the system performs an automatic assessment of its cryptoresistance, and the result is visualized in the upper right corner.
A strong password is one where the light indicator is lit in green (strong).
Note: If no password is entered, the contents of the package will be encrypted if the execution of this process is confirmed by the end user. In this case, the user password is only an auxiliary element of the security system.
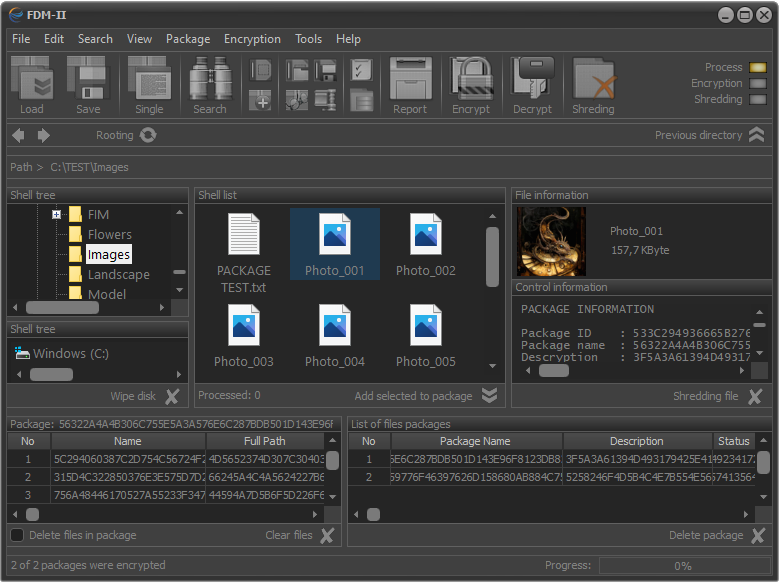
Fig.4. Encrypted metainformation in selected package.
The decryption of the meta data in the package is carried out by selecting Encryption - Decryption meta data from the main menu, using the quick link F10 or clicking on the Decrypt button located on the control panel.
Contents Next >