LE3.1.1.4
ENCRYPTION METHODS

Basic Encryption Methods
1. Encrypt using a password and use the built-in Windows features.2. Password encryption and choice of encryption algorithm and hash function.
3. Encryption using control string and choice of encryption algorithm and hash function. *
4. Encrypt using file. *
Strong encryption
The File Protect System uses a data protection method known as "Strong Encryption."
A similar method is used to encrypt classified information.
Unlike other applications, FPS encrypts each file.
This type of encryption guarantees much better protection than standard
approaches, because in some cases unauthorized access is virtually
impossible despite the cryptographic methods used.
To understand what "Absolutely secure encryption" is, we need to see how directory encryption is done.
One of the most commonly used security methods is to keep the folder locked with a password.
However, this does not mean that the files stored in it as well as the subdirectories (if any) will also be protected.
If an unauthorized user breaks down the folder's security (can unlock it), he will get full access to all content.
The File Protect System does not lock the folder.
Folder encryption does not protect the folder as a disk space, but encrypts any files that are in the folder.
Encryption is done so that only authorized users are able to access the contents of the folder.
Virtually unauthorized users will have to overcome the protection of each of the files.
This process takes a lot more time than the default password break of a
protected folder. In many cases this is a physically impossible process.

Files in a folder can be encrypted with
one password and one encryption algorithm. but they can also be
encrypted with different passwords or use different encryption
algorithms.
Such an approach is called Object Relation Encryption (ORE), as each file is viewed as a digital object stored on the computer's hard drive or on external media.
In practice, a connection (relationship) is made between the selected encryption method and the file being encrypted.
Encryption processes can be performed under the direct control of the operator or be partially automated.
A Partially Automated Encryption Process is used in package file processing,
Select encryption mechanism
By "encryption mechanism" we will understand the sequence of actions that the system performs to encrypt digital data.
With File Protect System version LE, the following encryption mechanisms are available:
- Standard Encryption - With this mechanism, the user can select the encryption and hash function, and the password is manually entered.
- Use a control string - The user can choose the encryption mechanism and hash function, but the password is generated automatically. In this case, the password is called a Control String (CS). The password is created automatically based on a selected digital image area.
- Using a Key File - Encrypting data is done using a file. The file can be located on the hard drive or saved on external media. In this case, the file plays the role of a secret key.

Each of the so-called methods has both advantages and disadvantages.
Nevertheless, each one of them can be considered extremely reliable even for classified information.
Note: All matters relating to the creation, processing and storage of classified information, as well as the terms and conditions for access to it, are regulated by the Classified Information Protection Act.
Use control string
The use of a control string allows the user to generate a very long password using a digital image area.
Control string encryption requires the user to select "Use Control String" in the "Encryption Process Settings"
field in the Application System Settings Control Module. When this is
done, the indicator for use of the control string will be yellow.
In this case, the encryption will be performed with a selected
algorithm and hash function, but the password will be generated based
on a selected digital image area.
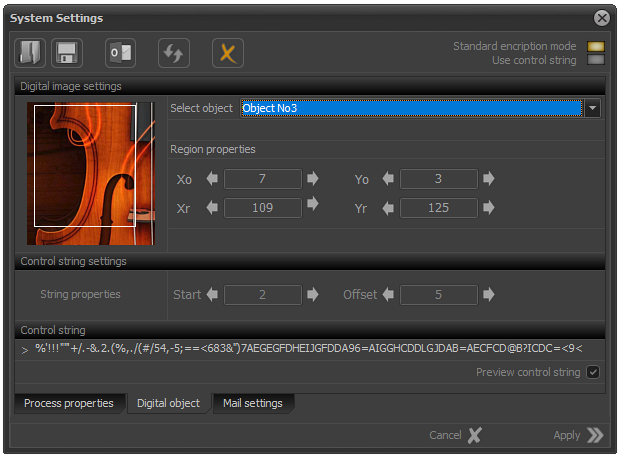
The next step is to set the parameters on the basis of which the system will create a reliable password.
In the LE version, this is based on a selected digital image area.
The first step in this process is to select an image.
In this case, the image is selected from a drop-down menu of four
predefined images. Each is designated as an object and a sequential
number.
Once the image is selected, it is necessary to define a rectangular area of it.
This can be done with the mouse or using the arrows located on both sides of the coordinate input fields.
The coordinates of the rectangular area are as follows:
- Xo - Horizontal position of upper left corner;
- Yo - Vertical position of upper left corner;
- Xr - Horizontal position of the lower right corner;
- Yr - Vertical position of the lower right corner;
In addition to the rectangular area, it is possible to enter two additional parameters: Start and Offset.
These two parameters set additional parameters for the application's internal security protocols.
In case of necessity, the automatically generated password can be visualized.
This is done by checking the "Preview password" field as shown on the image.
Use key file
The keyframe encryption mechanism is an unusual alternative approach to encrypting information.
In this type of encryption as a secret key, a local file or one that is located on an external media (flash memory) is used.
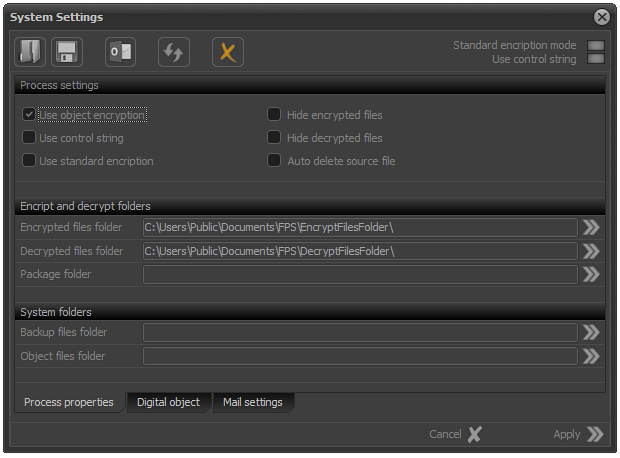
In order to set this encryption mechanism, it is necessary to check the "Use a key file" field and to exclude the fields using "Use control string" and "Standard encryption" as shown in the image.
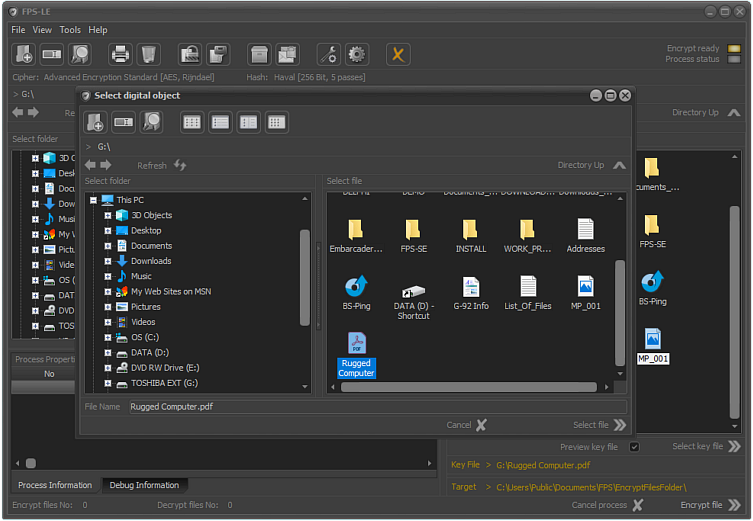
When the system enters the encryption mode where a key file will be used, the main menu view will change.
The "Password" field will be replaced with a field named "Key File". There will also be an additional panel with a button to select a key file.
The "Key File" and "File" captions will be in a different color than the other captions.
This is an indication that a key file is used rather than a password or a control string.
Encryption and decryption with a key
file is similar to a password, but instead a password should be
selected instead of a password.
To do so, click on the arrow located to the right of the "Key File" label, then select the file from the "Select file" panel to encrypt/decrypt and click on the arrow next to "Select".
If we want to make sure that we have chosen the correct file, we need to check the "Show key file" field.
All subsequent actions are detailed in the "Encrypting File Using a Password" section.
In this case, instead of a password, we have a file, but this in no way affects the speed at which the processes are performed.
Contents