LE3.1.1.4
SYSTEM SETTINGS

Basic settings
1. Encryption process settings.2. Set up directories that record the encryption or decryption results.
3. Set up system directories.
4. Select the basic parameters of the digital image.
5. Mail server settings. *
6. Custom e-mail settings.
7. E-mail Encryption Parameters Parameters. *
Manage system settings
For proper encryption process, correct parameters need to be set.
For this purpose, the parameters are entered and edited using the System Settings Control Module.
The system configuration control module for the LE version of the product consists of three main panels.
- Control Panel Process Parameters.
- Digital object selection panel.
- Input and Edit E-mail Parameters Panel.
At the top of the module is the control panel on which the system buttons are located, as shown on the image.

System buttons
1. Loading System Parameters.2. Save the system settings to the hard drive or external media.
3. Direct access to Microsoft Outlook to create a profile.
4. Restore the default settings.
5. Remove all the settings you have entered.
Process Parameters
When a file is encrypted or decrypted, by default, it is written to the specified directory.
The very process of encryption or decryption can be performed by
various mechanisms, according to the specific needs of the end user.
All settings related to file and folder processing are set in the "Encryption Process Parameters" panel.
The panel is divided into three sections as follows:
- Encryption process settings.
- Encryption and decryption directories.
- System directories.
The "Process Settings" section sets the parameters of the mechanism by which the selected files and folders will be encrypted or decrypted.
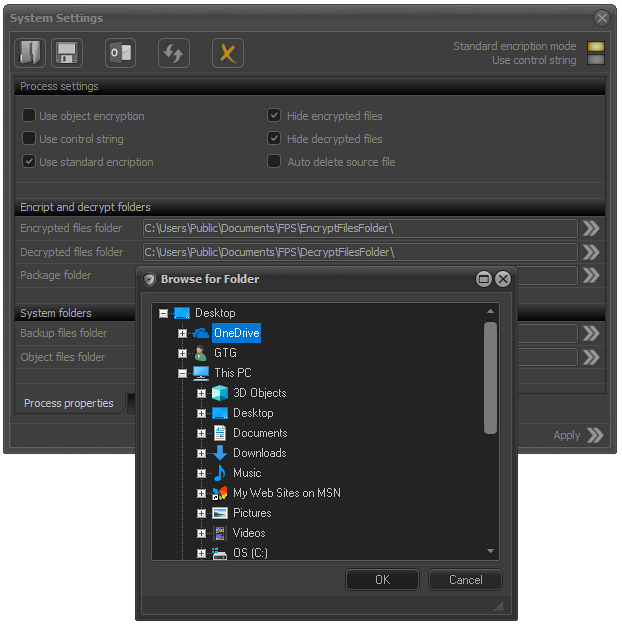
Additionally, you can determine whether
encrypted and decrypted files will be visible to other applications or
hidden. It can also be determined whether the output files will be
deleted or will be saved on the disk after finishing the process.
The "Encryption and Decryption Folders" section allows you to specify in which directories the results of the selected process will be recorded.
The "Encrypted Files Folder" box will enter the directory where the encrypted files will be saved.
The files that have been decrypted are saved in the Undefeated Files directory.
Backups will save backups of the output files if they are required to be stored.
Each of these directories can be changed by clicking on the arrow
located on the right of the field and selecting the directory in which
the results will be recorded.
Archives directories are used to record the archive created during the batch process.
The object directory can store the digital images that are used to generate a control string.
Note: Recording is allowed on external devices such as a flash drive or external drive, but when a device is selected, it must be physically plugged into the computer.
Digital Objects
With LE on File Protect System as digital objects used to automatically generate a secret key, only a single digital image is used.
Each of the digital images has its own ID.
In this version, it is permissible to use a maximum of four images.
Final users can choose from among them by using a drop-down menu, located in the "Digital Image Properties"
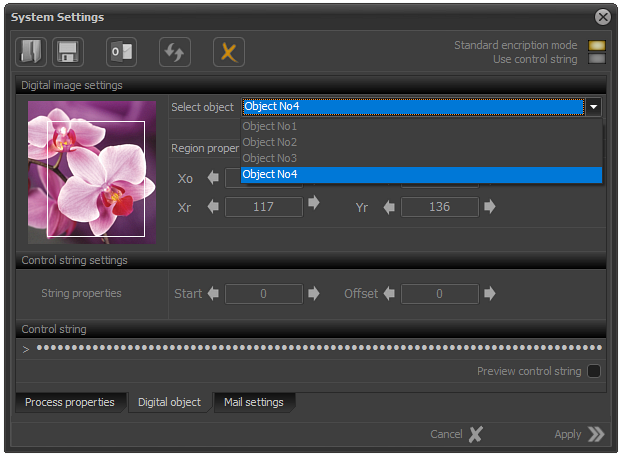
It is accepted that the generated secret key is called "Control String".
This is done in order to distinguish it from the known passwords.
Unlike passwords, the control string can not be created by the user. It is automatically generated based on a specialized algorithm that has a unique character.
For more information about automatically generating a control string using a digital image, read the "Encryption" section of this guide.
Note: In LE File of File Protect System, the length of the control string is limited. In practice, this means that the number of characters may be less than the allowable but can not be greater than the imposed limit.
E-mail settings
E-mail settings allow the user to enter and test the parameters of their Microsoft Outlook account.
This way, it will be able to send and receive secure messages and exchange encrypted files with other users.
In File Protect System LE, users can only use the e-mail resources provided by Microsoft to exchange encrypted messages.
For this reason, all advanced settings are not subject to adjustment.
They are written so that the user can be sure of their correctness but can not be changed.
What is allowed to the user is to change only the name of the e-mail and password.

Another feature of LE is that it is forbidden to use other defense mechanisms than standard ones.
In this case, the user is forbidden to use object-relational encryption, as well as the accompanying synchronization methods.
These methods are only available to users who are subscribed to the BeMail service.
Note: Although BeMail elements are used in the app, the full functionality of this type of postal service is not available to users. To activate all features, a monthly subscription and upgrading of the application to the appropriate version is required.