LE3.1.1.4
ENCRYPTED USING A PASSWORD
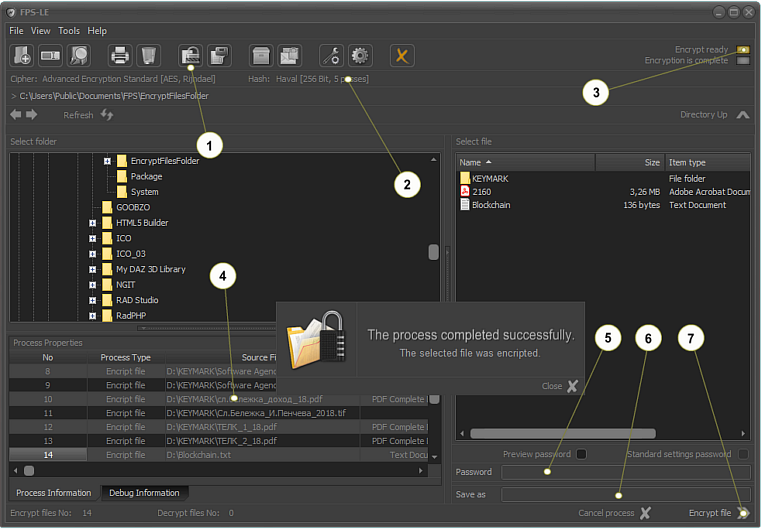
Functional blocks
1. Activation key for encryption mode.
2. Information about the used cipher and hash function.
3. Operating mode indicator.
4. Encryption process information in tabular form.
5. Password input field.
6. Destination where the encryption results are recorded.
7. Encryption process button.
Switch to encryption mode
Password and file encryption mode is the application's default mode.
The
AES encryption algorithm and hash function SHA-512 is set in the
default system settings. These parameters ensure high processing
efficiency. Even without changing anything in the system settings, the
selected files and folders will be protected reliably.
After the application is started, the operator can perform various
operations with local files such as copy, move, delete, rename, etc.,
but can not encrypt or decrypt data. This is a secure mechanism whose
task is to prevent random actions that would break the integrity of the
information.
To encrypt a selected folder, the system must go into the appropriate mode. Switching on is done by clicking on the "Encryption mode" button located on the control panel.
As a result of this action, the process indicator located in the right area of the panel will glow in yellow. The label "No Process Activated" will change to "Encryption Mode". In this way, the system is ready for subsequent encryption of selected files or folders.
Changing the current mode information as well as the yellow indicator
light indicates that the application is in the ready state to encrypt
files and folders.
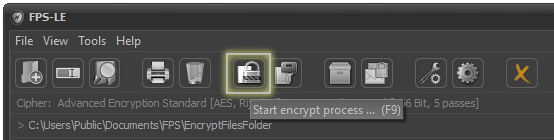
This action can also be performed using the system menu. To do so, select "Tools" and then set "Encryption Mode" as shown on the image.
Switching to encryption mode can also be done by pressing [ F9 ]
The next step is to set a trusted password to encrypt the selected file or folder.
ENCRYPTING FILES OR FOLDERS BY PASSWORD
Encrypt selected file
File encryption is automatically performed as a result of the following actions.
Select the file that will be encrypted in the "Select File" panel, then click on the "Encrypt" button or press the [ F12 ] key.
As
a result of these actions, the selected file will be encrypted. The
resulting secure file resulting from this process will be automatically
written to the encrypted file directory as specified in the
application's system settings.
The encryption process uses the entered password and the selected
encryption algorithm. When encryption ends, the system displays a
message that the process is completed successfully as shown on the
image.
The encryption process information is recorded in the table of executions. This information contains data about the source file, where and by what name and with what extension is saved, the duration of the process, etc.
When encryption is complete after the process is complete, the information in the "Password" and "Save as" fields will be automatically removed.
The reason for this is that in FPS each file can be encrypted with a different password, and it can also be saved with a different name or extension.
With critical information, encryption with different algorithms and hash functions is possible, according to specific needs.
Encrypt a selected folder (directory)
Folder encryption is automatically performed as a result of the following actions.
Select the folder that will be encrypted in the "Select File" field, then click on the "Encrypt" button or press the [F12] key.
As a result of these actions all files in the folder as well as those in the subdirectories will be encrypted with the entered password. Protected files resulting from this process will be automatically saved to the encrypted file directory as specified in the application's system settings.
IMPORTANT!
In cases where a selected folder is encrypted, all the files in the folder are encrypted.
There are no changes to the folder name.
The folder can be opened but its content will remain unavailable to the end user (the content will be protected).
When encryption ends, the system displays a message that the process is completed successfully as shown on the image.

As with file encryption, in this case the encryption process information is also recorded in the transformation map. However, when a folder is encrypted, information about the structure (the subdirectories of the selected folder) is also saved.
IMPORTANT!
When encrypting a folder, the resulting results store the output structure.
Although each file is encrypted, the result is written to the appropriate subdirectory as it is in the source folder.
Once the process is complete, the information in the "Password" and "Save as" fields is saved.
Encrypting password folders is more unreliable because the same password is used for all files in the selected directory. This is a prerequisite for a larger information surplus. To solve this problem in versions higher than SE, the password for each subsequent file is automatically modified. Thus, despite having a password, each file is encrypted with a different password, which makes the protection much more reliable.
Preview the password
Sometimes there are doubts whether
the password you entered is correct. In case of necessity the password
can be visualized. This is done by checking the "Password Preview field".
Note: The check string is inactive when using a standard encryption process. The field is activated when a control string is generated. This issue is subject to separate consideration.
Save Encrypted Files and Folders
Once encrypted, files and folders are saved in a pre-set directory.
This directory is listed in the "Encryption and Decryption Directories"
section of the "Encrypted Files" section of the System Setup Module.
By default, the directory where the encrypted files and folders are saved is:
This directory can easily be changed to meet specific needs.
To do so, click the "System Settings" button or press the [Alt+S] key combination.

Sequence of actions
1. Enable the System Setup Module.
2. Enable the device selection module and work directory.
3. Select a folder where the encrypted data will be saved.
4. Confirm selection.
5. Save the settings.
After activating the system settings set (as shown in the image),
another directory can be specified to record the encryption results.
This is done by clicking the arrow located at the right of the Encrypted Files box under Encryption and Decryption Directories.
After the Directory Selection window opens, the folder in which we will record the results is selected.
We confirm the selection by pressing the "OK" button and save the settings by clicking on the "Save" button.
Example:
It is necessary to store encrypted personal data on an external device (flash memory).
After the device is turned on, the operating system recognizes it as a G:\ logic device.
The directory in which we will record the encrypted information is G:\DEMO\
We open the system settings panel and choose for a directory where we will save the encrypted G:\DEMO data.
We confirm the selection by recording the system settings ("Save" button in "System Settings").

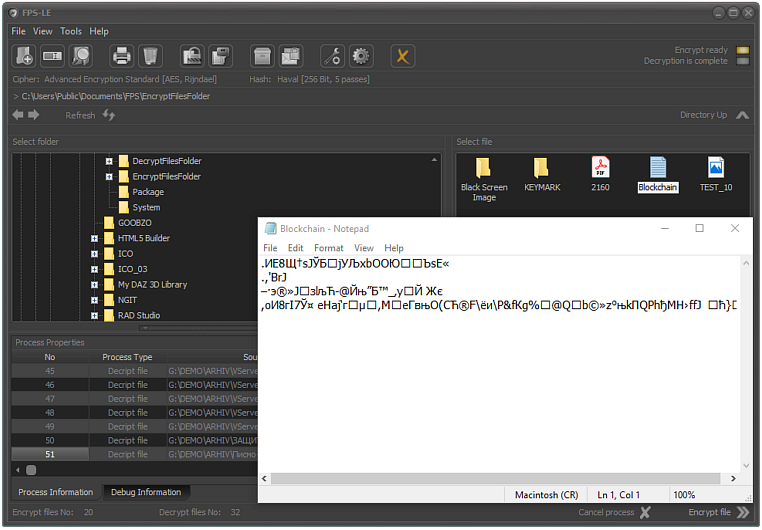
After the device and directory selection so made, all encrypted 2485 files are saved in G:\ DEMO \ as shown on the image.
What is important to know that whether we encrypt a file or folder, if it already exists in the directory where the results are written, it will be overwritten without requiring confirmation.
IMPORTANT!
Whether we use a default folder or set another folder, after the
encryption process is completed in the "File Selection" box on the main
menu, the contents of the directory in which the results are saved are
displayed.
The output data is retained in the type in which it is recorded (in unencrypted form). Their deletion is only performed if explicitly indicated.
Note: If you delete the source data, it is possible to generate backups in an unencrypted form. You can learn more about this and other actions in the System Settings tab.